What Best Describes Ips Comparing to Ids
Although the heartbeat can appear in different phases of the connection setup intrusion detection and prevention systems IDSIPS rules to detect heartbeat have been developed. Disabled VTP V2 Mode.

Ids Vs Ips A Comprehensive Guide To Network Security Solutions
An attacker builds a botnet comprised of zombies.

. 7 VTP Operating Mode. Press the button to proceed. In case you didnt find this course for free then you can apply for financial ads to get this course for totally free.
Which statement describes a distributed denial of service attack An attacker sends an enormous quantity of data that a server cannot handle. To display the VTP configuration information we can use the show vtp status command. Client VTP Domain Name.
Study-ccna VTP Pruning Mode. Your browser does not support JavaScript or it is turned off. Non SQL Injection Errors.
Switchshow vtp status VTP Version. SQL and Command Injection Web App Hacking. Hello Peers Today we are going to share all week assessment and quizzes answers of IT Security Google IT Support Professional course launched by Coursera for totally free of cost This is a certification course for every interested student.
Disabled VTP Traps Generation. An attacker builds a botnet comprised of zombies. 2 Configuration Revision.
Application security describes security measures at the application level that aim to prevent data or code within the app from being stolen or hijacked. Due to encryption differentiating between legitimate use and attack cannot be based on the content of the request but the attack may be detected by comparing the size of the. Which statement describes a distributed denial of service attack An attacker sends an enormous quantity of data that a server cannot handle.
3 Maximum VLANs supported locally. IDS Firewall and Honeypot Evasion. One computer accepts data packets based on the MAC address of another computer.
Although Secure SDWAN is indeed cheaper making it a correct answer that is not the best answer as. OWASP Top 10 and Beyond. One computer accepts data packets based on the MAC address of another computer.
When comparing MLPS Multiprotocol label switching to Secure SDWAN Software-defined wide area network SDWAN provides a more secure less expensive and faster solution. It should also be noted that some traditional IT security products can be deployed in OT systems if used in limited ways. Evasion Testing Techniques.
It encompasses the security considerations that happen during application development and design but it also involves systems and approaches to protect apps after they get deployed. Common Web Server Attack. IDS Overview and Detection Methods.
An attacker views network traffic to learn authentication credentials. MLPS communications and transactions are supported in the SDWAN environment. Threat Intelligence also known as security threat intelligence is an essential piece of CTI for a cybersecurity teamAccording to Recorded Future threat intelligence is the output of the analysis based on detection identification classification collection and enrichment of relevant data and information Threat intelligence helps a security team understand.
Nous voudrions effectuer une description ici mais le site que vous consultez ne nous en laisse pas la possibilité. OT cybersecurity products include asset discovery vulnerability management unidirectional gateways and application and device control. An attacker views network traffic to learn authentication credentials.
255 Number of existing VLANs. For example devices such as the IPS might only ever be operated in passive IDS mode.
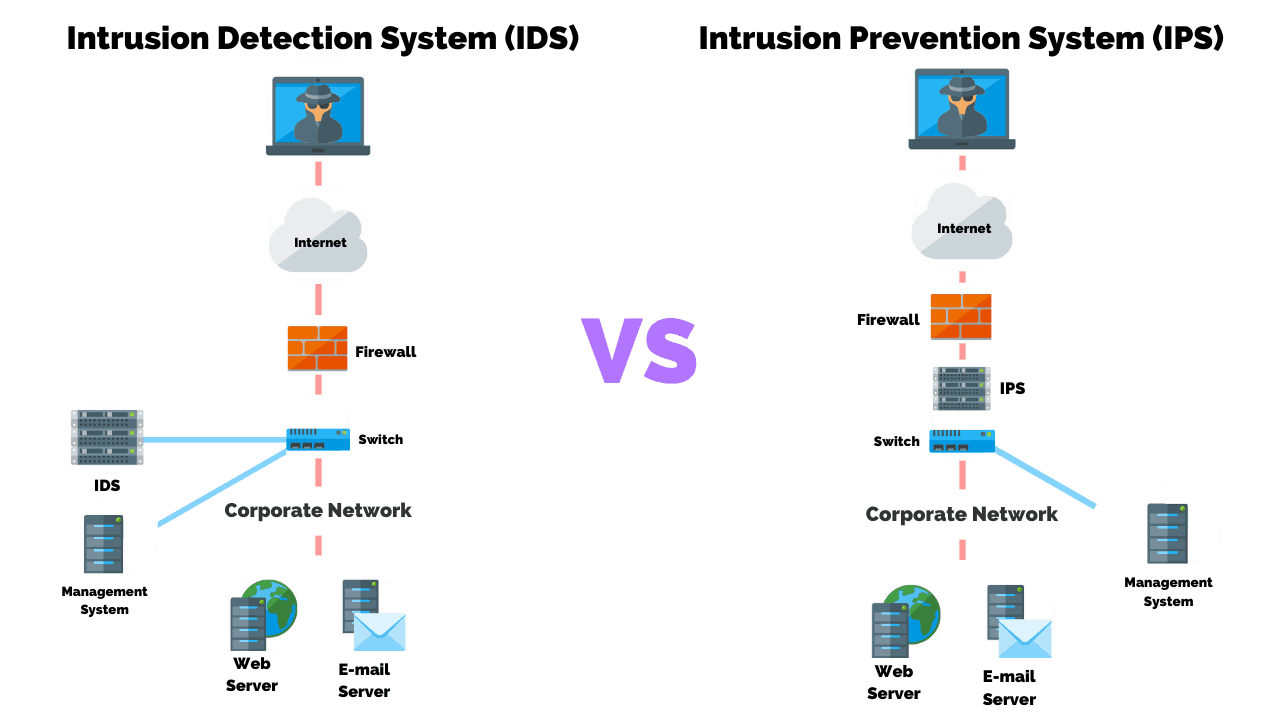
Intrusion Detection Vs Prevention Systems What S The Difference
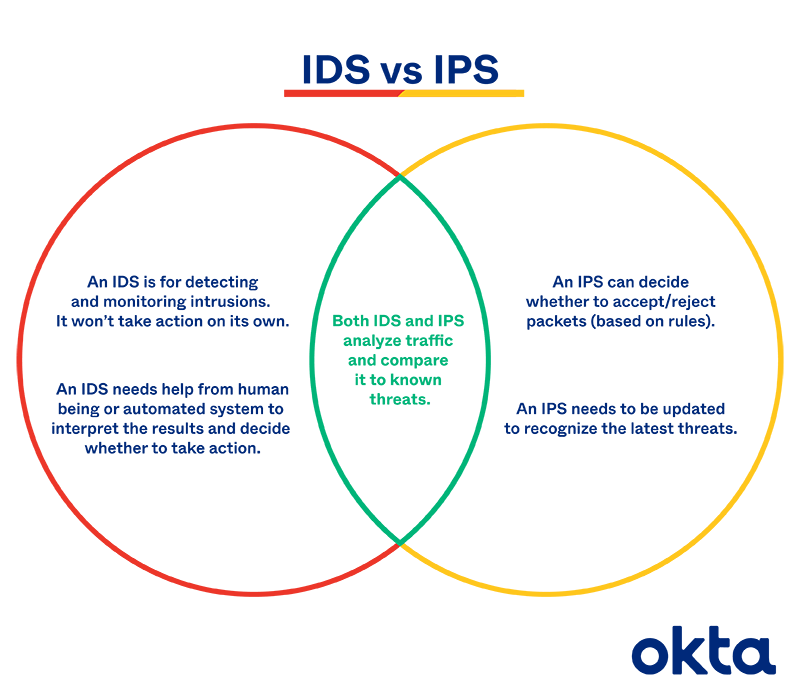
Ids Vs Ips Definitions Comparisons Why You Need Both Okta


Comments
Post a Comment